When an entrance to an office building, healthcare facility, or school isn’t secure, the facility is vulnerable and ultimately could be liable if something bad happens as a result of negligence.
A great way to help secure a facility’s entrance is to use a visitor management system (VMS) to document all visitors. Once the software is set up and in-use, you’ll enjoy the many benefits of the system, such as quick and easy sign-in, secure identification, reliable data access, and convenient reporting.
But, in order to utilize the full benefits of the visitor management software, you’ll want to steer clear of these worst practices with relation to visitor management and building security.
1) Having multiple visitor entrances. Typically, businesses will have a main entrance and exit, as well as some emergency exits, depending on the size/capacity of the building. Businesses that have multiple entrances put themselves at a higher risk than businesses that utilize one main entrance to funnel visitors to a front desk or lobby. Securing multiple entrances is hard to do and potentially expensive if each entrance needs a visitor management system and security personnel. Plus, it gives people with bad intentions the opportunity to find a weak spot in any of the entrances to gain access to your facility.
2) Not having the visitor management system close to the main entrance. Most likely, visitors are coming through a single entrance to your facility. When they get in the front door, they should immediately see the visitor management system with signage about what is expected during their visit. Having the visitor management system out of view would be confusing and inefficient.
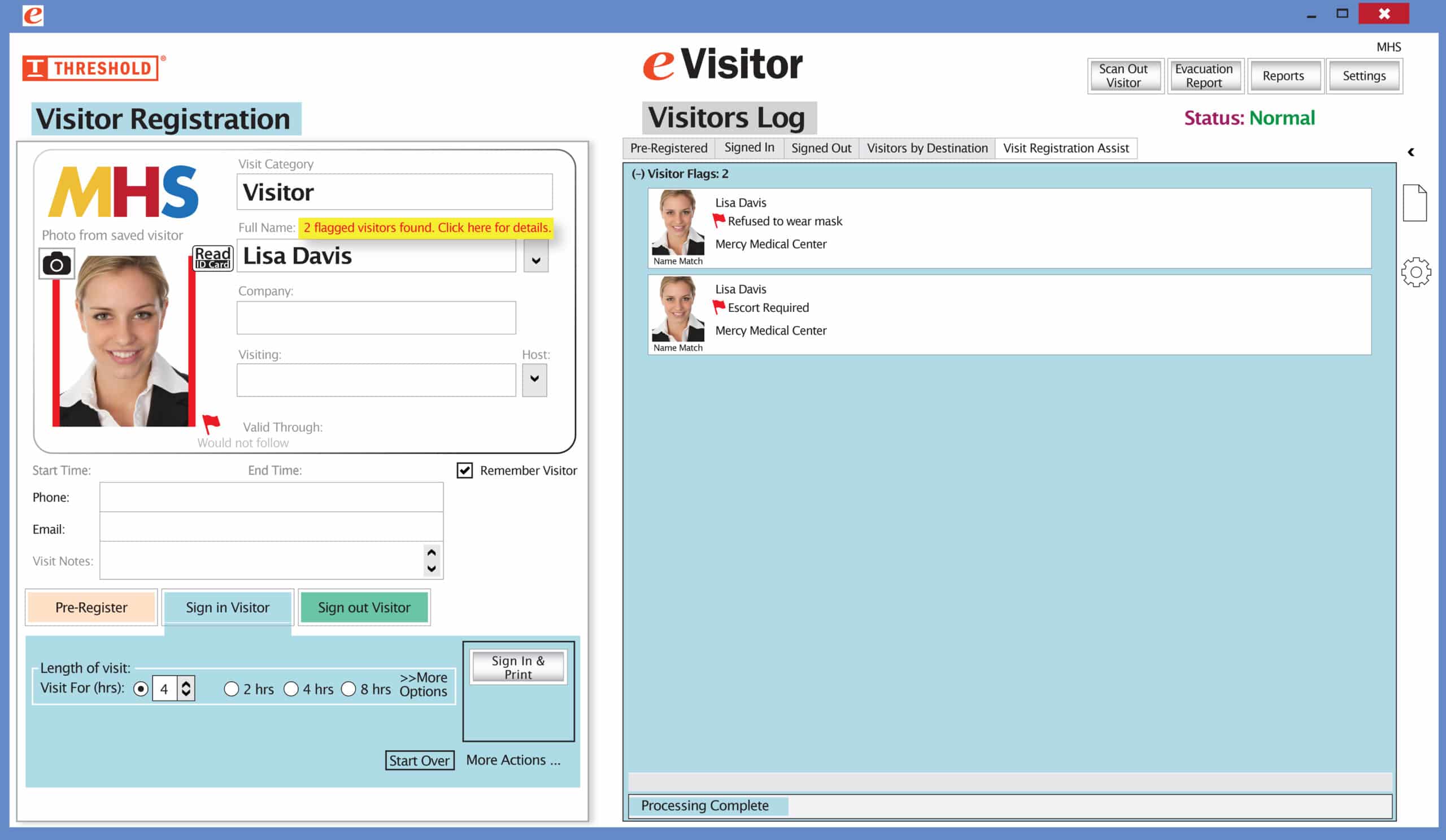
3) Not documenting every visitor. Every guest, contractor, vendor, parent, relative, friend, delivery person, or potential new hire that comes to your building should be documented in a visitor management system. It doesn’t matter if the same visitor comes so often that the front desk receptionist knows the person by name. Every visitor should be documented. The reason isn’t always because the front desk receptionist doesn’t know the visitor. For example, if there were an immediate need to evacuate the building, it would be important to know who was in the building at the time. A VMS can do this for you.
4) Granting unexpected visitors access to your building. Does your organization have a walk-in policy? How do you handle unexpected visitors? Many companies do not have a proper system in place to account for unannounced visitors, which can greatly inconvenience your security & IT department if they aren’t equipped with ways to handle walk-ins.
5) Failing to use a driver’s license scanner. Hand-keying the visitor’s information has the potential for human errors and takes too much time. While not impossible to do, why not make the process foolproof by using a driver’s license reader, so critical fields aren’t missing and everything is spelled correctly? In addition, some scanners even capture the photo from the license, which adds to the facility security.
6) Not capturing additional information about the visit beyond the driver’s license. Scanning a license captures a lot of important information about the visitor to your facility. However, who are they there to see? What company are they from? What time did the visitor arrive? What part of the building are they going to? It is possible to document all these things on a visitor badge (and the corresponding visitor reports) so more information is known about a visitor beyond who they are.

7) Failing to print a visitor badge to wear while at the facility. Capturing driver’s license data and the particulars about a visit are great for knowing who is in your facility at any given time and for what reason. What about for the employees in the facility who don‘t recognize the visitor? Especially in larger facilities, it is difficult to know everyone who works for a particular company, healthcare facility, or school. If an employee sees a stranger who is not wearing a visitor badge, they may wonder who they are and what they are doing there. At best, not identifying visitors arouses employees’ curiosity and, at worst, leaves people and property exposed to potential harm. A custom-printed visitor badge, which includes a photo, clearly identifies the visitor.
8) Ignoring the reports available for visitor data. A major reason why a computerized VMS is an upgrade over manual sign-in books is the ability to analyze visitor data electronically. There is complete data on every visitor that has ever been to a facility, and that data can be mined to identify trends. Most visitor management systems can generate custom reports and allow them to be shared with security personnel very easily.

Besides the obvious security reasons for knowing who is in the building at any given time, there are other non-security benefits for the visitor data. For example, visitor reports can be generated about outside contractors to verify arrival and departure times to ensure they have been on the job as invoiced. Oftentimes if organizations are still relying on manual processes to document and check in visitors, data can become cumbersome to log or get logged incorrectly. Failing to document who people are, why they are there, and where they are going on-site can leave organizations vulnerable without that data.
If you’ve had to admit your visitor management falls under any of these bad practices, THRESHOLD can help. Our eVisitor Software can affordably increase your building security and help you always know who is in your building. Request a free demo today!