In an age of digital transformation, it’s easy to assume that old-school methods like a visitor log book have lost their place. But the reality is quite the opposite. For many businesses, especially those with physical locations or sensitive operations (ex. Healthcare Facilities or Government Buildings), a reliable visitor log system is still one of the most effective tools for ensuring site security and accountability for the following reasons:
Tangible Accountability
Digital systems can fail. Visitor management software could stop working for maintenance, software issues, or due to power outages. A well-maintained, secure log book provides an immediate, physical record of who entered the building and when. In critical situations such as emergency evacuations, quick access to visitor data without relying on tech infrastructure is invaluable. The log book can also serve well during audits as proof of visitor documentation by the visitors themselves.
Privacy and Simplicity
Sometimes, simplicity is more secure. A traditional log book, especially when designed with privacy in mind (e.g., hiding previous entries like the Confidential Sign-in Book), avoids risks tied to data breaches or system hacking. It’s a straightforward, low-tech solution that doesn’t require passwords, updates, or training.
A customer of ours, a family law firm in Chicago, switched to the Confidential Sign-in Book after clients expressed concerns about names being visible to others in the waiting area. This simple change aligned with client confidentiality expectations and boosted trust.
Regulatory Compliance
Certain industries, like healthcare and legal services, still require paper-based records for compliance with regulations or internal policies. A secure log book helps ensure these standards are met without adding complexity.
Trust and Transparency
Visitors often feel more comfortable signing a physical log — it’s familiar and transparent. They know exactly what data is being collected because they are filling it in. There is also less concern about where it might end up in cyberspace or their sign in being tied to a database.
Another customer of ours, an elementary school in rural Vermont, implemented our visitor management software for documenting visitors — but still kept a paper log book at the front desk. Many grandparents visiting for school events preferred the simplicity of writing their name rather than navigating a tablet.
What Is a Visitor Log Book?
A visitor log is a record-keeping system used to track everyone who enters and exits a facility. Maintaining an accurate log of who’s on-site, when, and for what reason is critical for facility security.
A visitor log book traditionally sits at the reception desk, where guests manually sign in, providing basic details such as their name, the person they’re visiting, time of arrival, and departure.
Why It Matters: Real-World Impact
One of the best ways to understand the importance of a visitor log book is through real-world examples. A couple years ago we published a case study detailing how a school in Pennsylvania improved its sign-in security, which was a concern for parents. The school did this by implementing the Confidential Visitor Sign-In Book.
Case Study Snapshot:
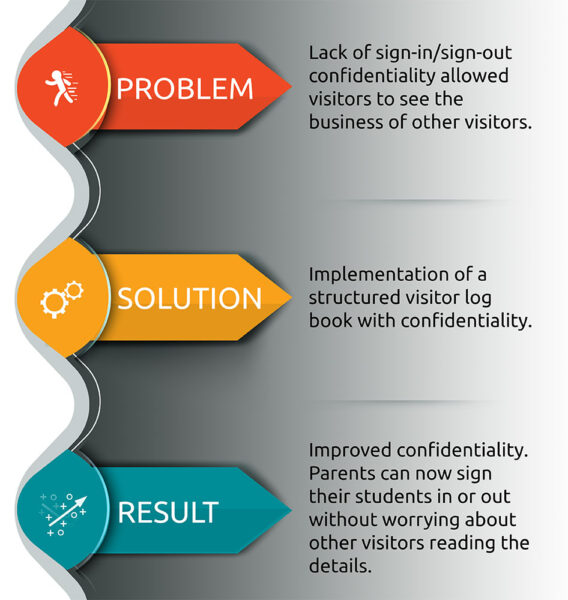
This simple change made a measurable difference. Christine A. Stosek, administrative assistant to the principal of Tobyhanna Elementary Center in Pocono Pines, Pennsylvania, said “our parents can now sign their students out without worrying about others reading the names of students leaving our building.”
Paper Sign-In vs. Visitor Management Software: Which Is Right for You?
Choosing between a physical visitor log book and a digital system depends on your facility’s size, budget, and security needs.
Feature
Paper Log Book
Digital Visitor Log
Cost
Low
Higher Upfront Cost
Ease of Setup
Instant
Requires Hardware/Software
Data Retrieval
Manual
Searchable and Exportable
Security & Privacy
Prone to Snooping
Encrypted and Secure
Customizable?
Yes
Yes
For small to mid-sized businesses, a well-designed visitor log book offers a cost-effective, low-tech solution that gets the job done.
How does the Confidential Visitor Sign-In Book work?
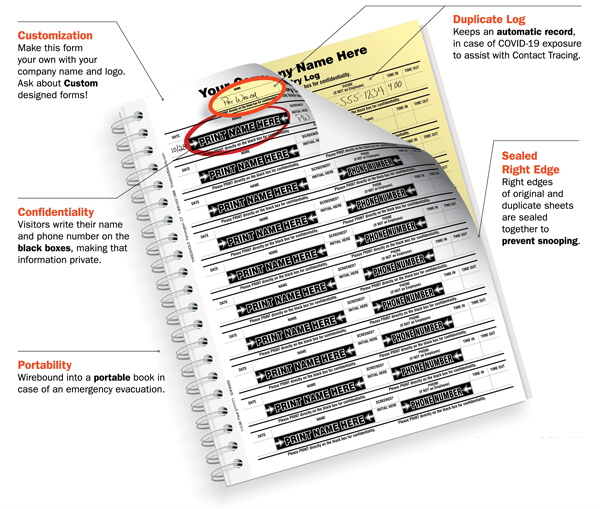
Two-part carbonless forms perform two jobs in one step – the white first part contains a “blockout” pattern on all names to protect the confidentiality of those signing in. The yellow second part provides an automatic duplicate record that lets only you and your staff see the names that are “blocked out” on the white first part. The right side of the two-part set is glued together as an additional confidentiality measure, protecting against subsequent visitors peeking inside.
What makes THRESHOLD log book “confidential” and secure?
A security blocking pattern is printed over the fields on the top sheet of the product that contain sensitive information (visitor’s name, who they are there to visit, etc.) The security blocking allows visitors to see that the pen they are using is actually writing something (thanks to a little bit of white in the pattern). However, it prevents others from deciphering what is being written, such as visitors who sign in later; they can’t read any sensitive information on the top sheet. In addition, the right edges of the original and duplicate sheet are sealed together to further prevent snooping.
Summary
Whether you choose a paper-based visitor log book or go digital, having a consistent visitor management process is critical. It protects your assets, ensures compliance, and shows professionalism to every guest who walks through the door.
While digital tools offer speed and integration, a secure visitor log book provides reliability, simplicity, and peace of mind. In many cases, the best approach is a hybrid one — where physical and digital systems work together to ensure both convenience and security.
Want to see how a simple visitor log book improved one school’s security and confidentiality? Read the full case study here.

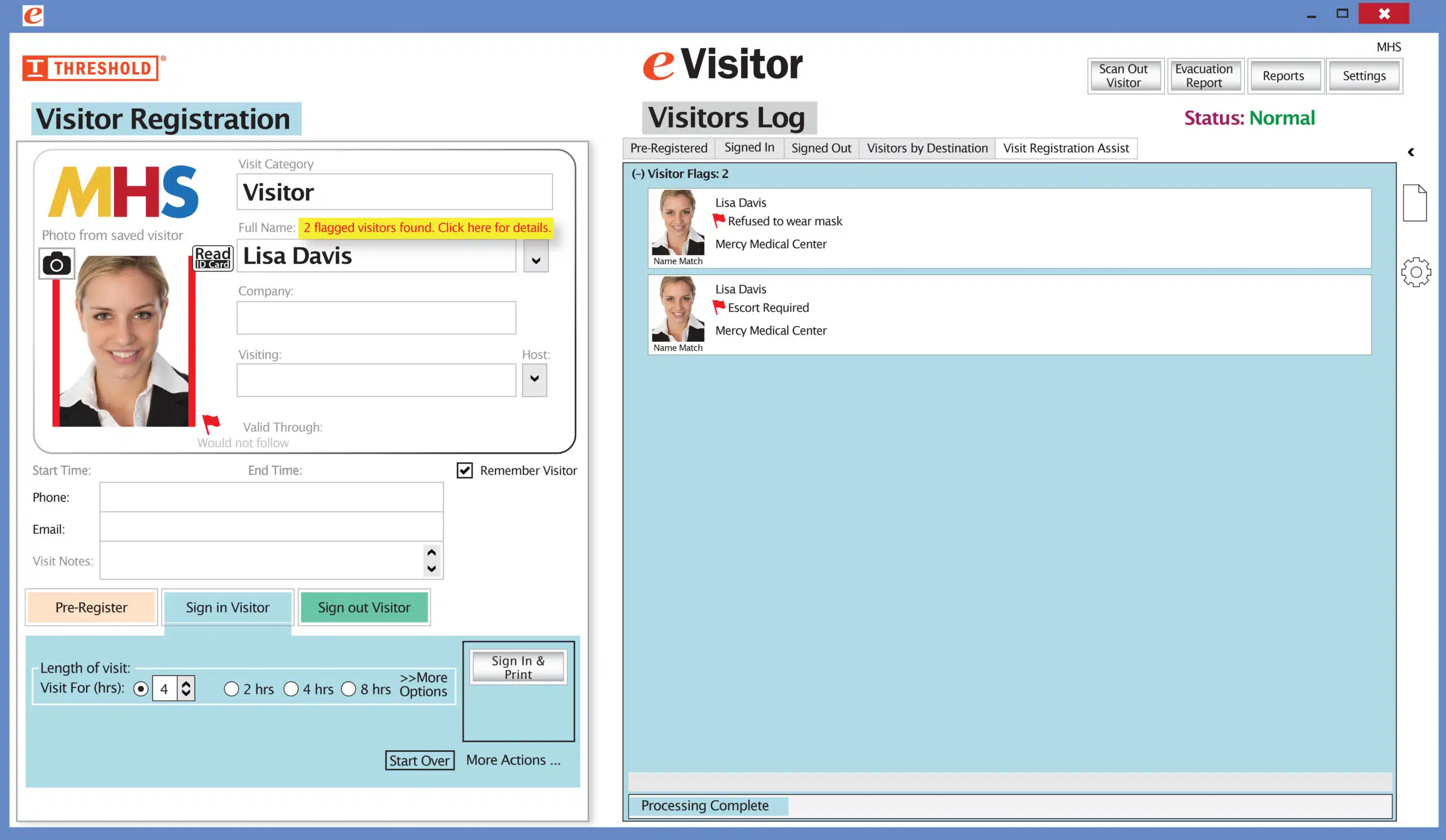 It’s easy and free to activate this feature. Simply call us and ask for “Red Flag, No Badge” to be turned on. Once it’s on, the above pop-up will come up when a red flagged visitor comes back. No badge will print and the attendant will need to follow the facility’s policy for handling red flagged visitors.
It’s easy and free to activate this feature. Simply call us and ask for “Red Flag, No Badge” to be turned on. Once it’s on, the above pop-up will come up when a red flagged visitor comes back. No badge will print and the attendant will need to follow the facility’s policy for handling red flagged visitors.