- Identify the risks
- Protect the assets and services
- Detect what is happening, when it is happening, and where it is happening
- Respond with the appropriate level of resources
- Recover from the event to keep the essential services operational (Continuity of Operations Plan or COOP) for the public good

A successful security assessment of a healthcare facility should include these three components (in collaboration with your security team):
If the objective is “personnel safety,” identify the types of people in the building and where they congregate, for example, smoking areas, break rooms, and/or parking lots. Defining objectives cannot be overlooked or blended into other phases. It’s critical that security teams and management work together to clearly identify objectives.
2. Identification of the threats, vulnerabilities, and risks
Threats are defined as an event that would significantly reduce or destroy the functionality of a healthcare facility. These could be naturally occurring or happen because of people’s actions. Vulnerabilities include where and what would be attacked and how to prevent it. Risks are identified as what an attack would do to operations and what is likely or unlikely.
In this step, you identify the types of dangers to personnel. Their likelihood should be listed and given a “rating” as to their probability. The rating system is determined by the security team, but it must make sense and be scaled.
The Department of Homeland Security lists the following as the most likely threats to a healthcare facility:
- Active shooters
- Disgruntled or violent persons
- Bomb detonation
- Arson
- Criminal violence
- Proximity to neighborhood violence
- Dangerously-close proximity of the hospital to other high value targets such as military bases, power stations, and government buildings.
At this step in the planning, a meticulous review of resource allocation is required to include the “rating” designators discussed in step 2 to rate the likelihood of one event and its impact versus another. The team should take into account the single-loss expectancy and consider that against the annual rate of occurrence to compute a loss expectancy over a year’s time. Once the decision is agreed upon, it’s time to decide on the types of solutions to implement at your facility.
Solutions
- Access control systems
- Visitor management software
- Perimeter detection systems and alarms
- Intelligent lighting systems
- Sensors on doors and windows
- Surveillance cameras
- Barriers
One of the solutions mentioned above is using visitor management software. eVisitor Software is a stand-along visitor management systems that can affordably increase your facility security and help you always know who is in your building. eVisitor makes it easy for facilities to log, identify, track, and run reports on visitors. Watch this video to learn more, then request a free demo today!


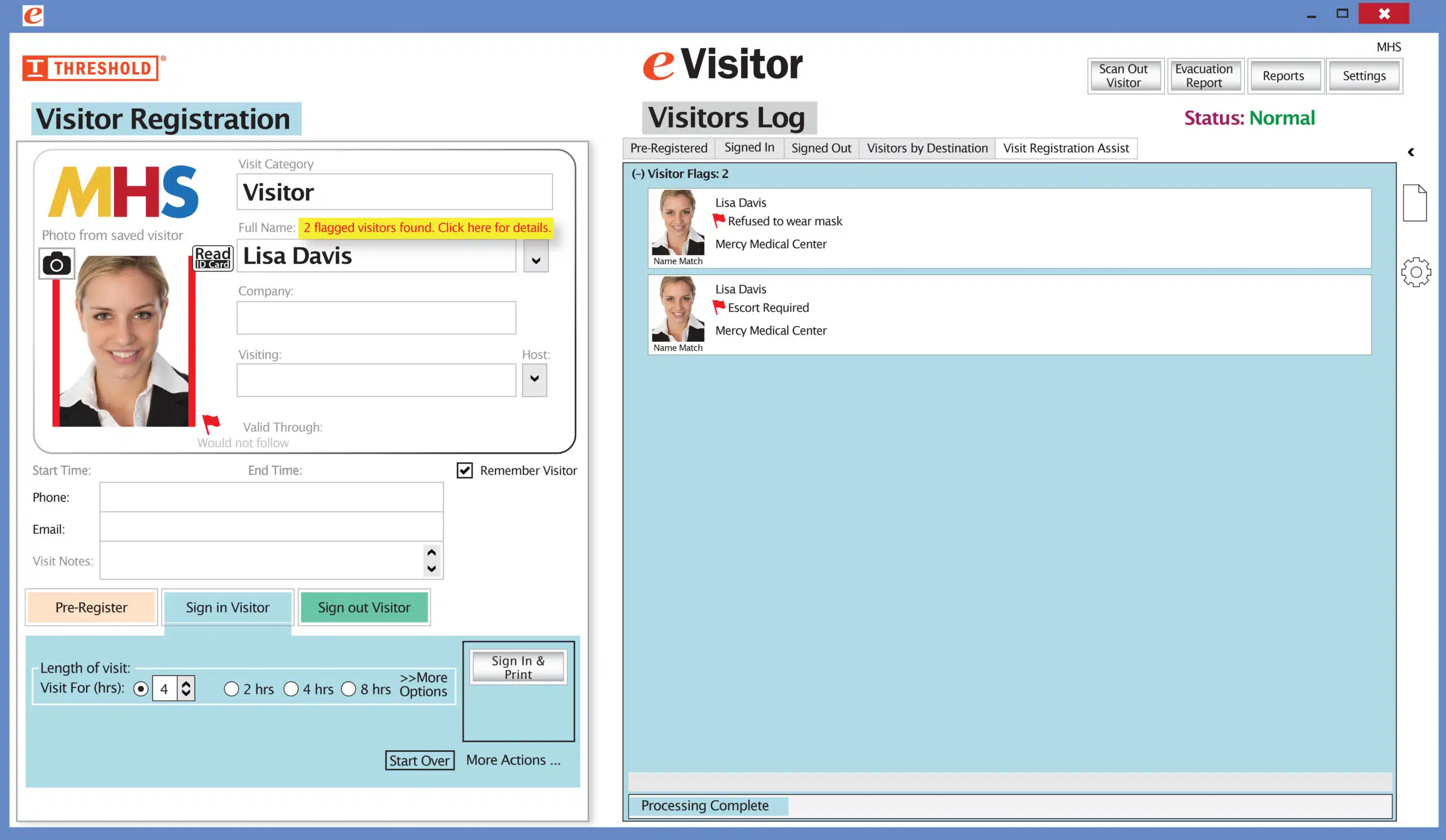 It’s easy and free to activate this feature. Simply call us and ask for “Red Flag, No Badge” to be turned on. Once it’s on, the above pop-up will come up when a red flagged visitor comes back. No badge will print and the attendant will need to follow the facility’s policy for handling red flagged visitors.
It’s easy and free to activate this feature. Simply call us and ask for “Red Flag, No Badge” to be turned on. Once it’s on, the above pop-up will come up when a red flagged visitor comes back. No badge will print and the attendant will need to follow the facility’s policy for handling red flagged visitors.